AI Code Generation Boosts Speed But Adds Cybersecurity Risks.
AI code generation is transforming software development, offering speed and scale like never before. Yet beneath the surface lies a growing wave of cybersecurity risks that remain largely overlooked. While the hype celebrates efficiency, conversations about the security pitfalls are conspicuously missing.
The adoption of AI code generation is spreading like wildfire. For instance, nearly 25% of newly written code at Google is now AI-generated. These tools help developers accelerate delivery, reduce boilerplate, and even support non-coders in building applications. But with this power comes risk—ranging from insecure logic and unpredictable outputs to supply chain vulnerabilities and exploit automation.
This blog unpacks 10 of the most urgent cybersecurity risks introduced by AI code generation – based on recent research, real-world findings, and secure development best practices. Concrete mitigation strategies are also explained to enable leaders make their AI code generation process more secure.
What Is AI Code Generation, and Why Is It Gaining Traction?
AI code generation (sometimes also called Vive Coding) refers to the use of large language models (LLMs) and code-specific AI assistants to automatically suggest, write, or complete code based on natural language prompts or partial code snippets. These tools are trained on massive corpora of source code and documentation from public repositories, forums, and documentation.
Popular examples of AI code generation tools include GitHub Copilot, Replit Ghostwriter, Tabnine, and Cursor. These tools improve developer productivity by:
- Reducing boilerplate and repetitive coding tasks
- Speeding up prototyping and experimentation
- Supporting junior developers or non-engineers in writing basic functions
- Enabling multilingual code generation and translation
Despite the immense productivity gains, developers and organizations must also consider the security implications. AI Code generation is not immune to vulnerabilities—and in some cases, it can scale them. That’s why understanding the risks is essential before adopting these tools at scale.
The 10 Most Critical Cybersecurity Risks of AI Code Generation
Below are the ten critical cybersecurity risks associated with the most critical cybersecurity risks introduced by AI code generation, each demanding close attention and proactive mitigations.
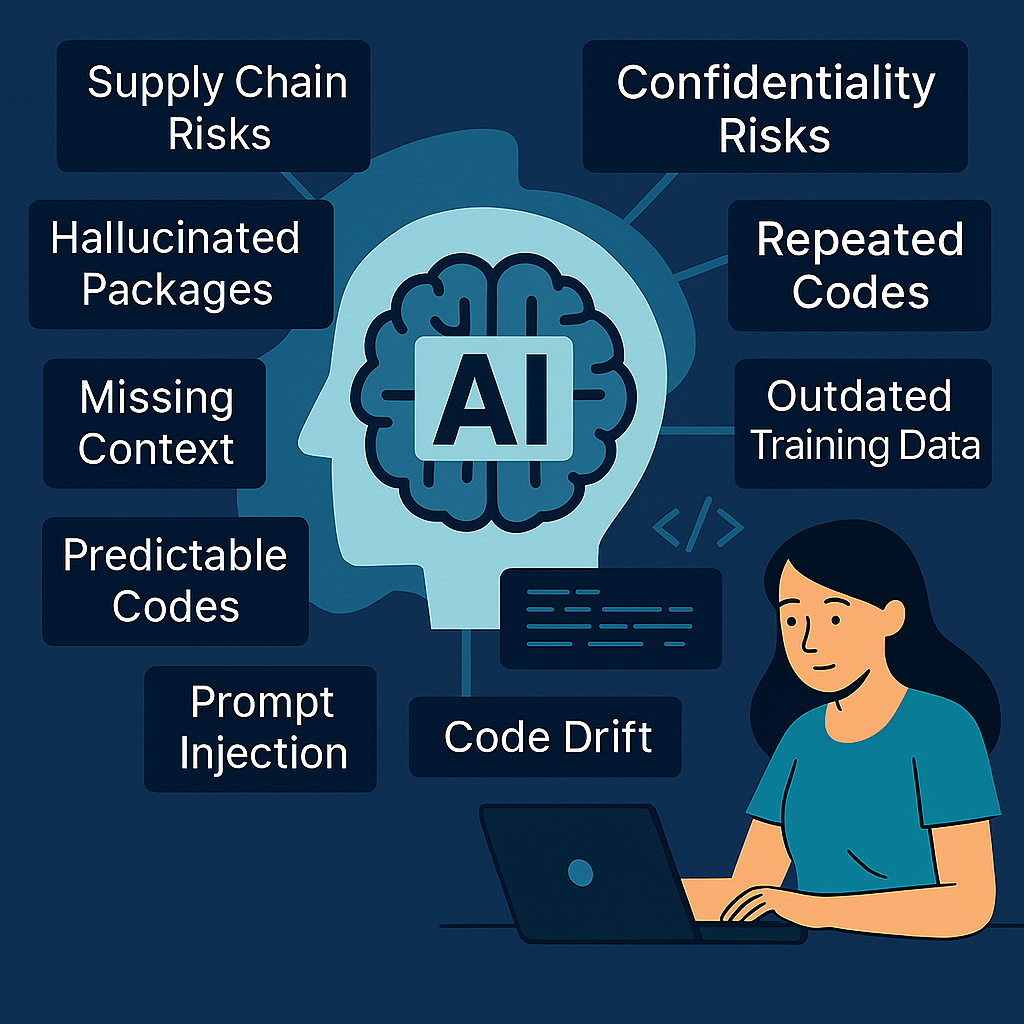
Figure: cybersecurity risks associated with AI Code Generation
1. Supply Chain Risk: AI Generated Code May Have Insecure Dependencies
Issue:
- AI tools suggest outdated, vulnerable, or unverified open-source packages.
- Dependency recommendations are based on static pattern matching, not real-time vulnerability scanning.
- Tools often lack awareness of organizational security policies, internal whitelists, or industry compliance standards.
- Third-party libraries can easily infiltrate core applications without proper vetting.
Risk:
- Developers may unknowingly integrate packages with known CVEs, leading to remote code execution (RCE) or privilege escalation vulnerabilities.
- A single compromised package can infect multiple systems across CI/CD pipelines and production environments.
- Outdated dependencies may cause regulatory non-compliance (e.g., GDPR, DPDP, HIPAA, PCI DSS).
- Legal, reputational, and financial damages could result from supply chain attacks exploiting these weaknesses.
AI Code generation often recommend outdated or vulnerable open-source packages without real-time security scanning. These unsafe libraries can introduce critical vulnerabilities and may violate organizational security policies. Without proper vetting, abandoned or unpatched components risk embedding hidden threats into the software supply chain.
2. Hallucinated Packages: May Result in Non-Existent Packages in Codebase
Issue:
- AI sometimes invents non-existent package names that appear legitimate.
- Research shows 5%–25% of packages suggested by LLMs may be fabricated.
- Developers may not verify the authenticity of package names before use.
- These hallucinated names can resemble popular or trusted libraries, increasing their believability.
Risk:
- Attackers can register these non-existent names and inject malicious code.
- Since the names appear plausible, they often evade manual review.
- Malware embedded in slopsquatted packages can exfiltrate data, execute remote code, or create persistent backdoors.
- Once published and pulled into a build, these packages compromise CI/CD pipelines and production systems.
This emerging threat, called “slopsquatting,” allows attackers to weaponize AI hallucinations. When a developer accepts a hallucinated package import created during AI code generation, a malicious actor can pre-emptively publish it with malware. Because the name looks plausible and code seems to work, detection often happens too late.
3. Missing Context: AI May Miss Business, Architectural and Compliance Requirements
Issue:
- AI code generation may not be aware of regulatory requirements (e.g., GDPR, HIPAA, PCI DSS).
- They may not consider application-specific threat models and risk scenarios.
- They may overlooks cross-module, cross-file data flows, and integration points.
- They may not be aware of the enterprise architecture standards or specific business logic.
- They does not understand user role segmentation, access control models, or sensitive data pathways.
- AI code generation process may not have access control at granular level (e.g. access control at objects or functions level)
Risk:
- Insecure code is silently introduced, leading to data leaks, compliance violations, or logic flaws.
- Gaps in authorization, auditing, or exception handling due to missing application-specific context.
- AI may skip critical security features (e.g., logging, encryption) because it lacks understanding of system boundaries.
- Systems may pass functional tests but fail security reviews, increasing risk of production incidents or breaches.
Most of the AI code generation lacks true contextual awareness. They don’t understand user roles, data sensitivity, or regulatory obligations (e.g., GDPR, HIPAA). This leads to code that appears secure but violates compliance standards or creates business logic vulnerabilities. For example, an AI might skip logging for failed logins, creating blind spots in audit trails.
4. Predictable Code Generation: When AI Code Becomes an Exploit Template!
Issue:
- AI code generation often follows consistent and easily recognizable patterns.
- It lacks built-in code diversification, randomness, or obfuscation mechanisms.
- Generated outputs frequently reflect common patterns found in public training data.
- AI tools don’t add anti-debugging, anti-reconnaissance, or evasion logic unless explicitly prompted.
Risk:
- Attackers can quickly fingerprint and reverse-engineer AI-generated applications.
- The uniformity of output enables automation of exploit development across similar codebases.
- Predictable logic flows make vulnerabilities easier to discover and exploit at scale.
- Without defensive variability, systems become high-value, low-effort targets for adversaries.
Unlike skilled human developers, AI code generation doesn’t naturally add obfuscation, anti-debugging techniques, or code variation. Combined with reuse of insecure patterns from training data, this makes AI output a high-value target for adversaries who exploit uniformity.
5. Confidentiality at Risk: Hardcoded Secrets and Weak Encryption
Issue:
- AI sometimes suggests hardcoded credentials (e.g., API keys, passwords) in source code.
- AI may recommend outdated or insecure encryption and cryptographic algorithms like MD5, SHA-1 etc..
- Without prompts enforcing best practices, AI defaults to weak or legacy security patterns.
- Sensitive keys and credentials risk being exposed through public code repositories or insider threats.
Risk:
- Hardcoded secrets can be easily extracted by attackers, leading to unauthorized access.
- Using deprecated encryption algorithms compromises the confidentiality and integrity of sensitive data.
- Exposed credentials can enable lateral movement, privilege escalation, or data exfiltration.
- Organizations may fail security audits (e.g., SOC 2, HIPAA) and face regulatory penalties due to weak cryptographic practices.
AI generated-code often lacks awareness of best practices unless explicitly instructed. Without proper guardrails, AI code generation may result in sensitive values being inserted directly into code or default to obsolete algorithms. These errors can have serious consequences for confidentiality and compliance.
6. Technical Debt: Low Maintainability Due to Repeated Codes and Poor Comments
Issue:
- AI duplicates logic instead of using modular, reusable functions. This may increase the organizational code base size affecting the maintainability of the software’s.
- Comments generated during AI generated code may lack the nuances of human generated code (for example architectural context are often missing; or inline comments may not be sufficient)
- Code lacks consistency in style, naming conventions, and structure.
- Generated blocks can be disjointed, making integration across files difficult.
Risk:
- Future developers face confusion and high ramp-up time.
- Debugging becomes time-consuming due to poor documentation.
- Systems become fragile and hard to scale or modify.
- Over time, inconsistent and bloated codebases accumulate technical debt and increase long-term maintenance costs.
AI often generates near-identical code blocks instead of reusable abstractions and functions. It may neglect inline comments or architectural documentation, especially under vague or minimal prompts. Therefore AI code generation ends may results in hard-to-maintain systems, especially when AI-generated components evolve differently over time.
7. Old Mistakes Recycled: Outdated, Incomplete, or Biased Training Data
Issue:
- AI models are trained on vast but generic public codebases.
- AI assisted code may not incorporate the recent bug fixes related to libraries and packages
- Sources like GitHub and Stack Overflow often contain outdated or insecure coding practices.
- Insecure examples like weak hashing algorithms (e.g., MD5) and hardcoded credentials are learned unknowingly.
- AI cannot distinguish between secure modern patterns and legacy insecure ones unless explicitly instructed.
Risk:
- Flawed patterns and insecure defaults are replicated into new applications.
- Developers may unknowingly inherit vulnerabilities from AI-generated suggestions.
- Adoption of deprecated techniques (e.g., insecure random number generation, weak error handling) can propagate systemic weaknesses.
- Applications built on poor foundations face higher risks of data breaches, compliance failures, and technical debt.
Public code on GitHub and Stack Overflow forms the bulk of training data. Unfortunately, these sources contain insecure practices like MD5 hashing, hardcoded secrets, and poor error handling. AI tools absorb and reuse them unless prompted otherwise, baking yesterday’s mistakes into tomorrow’s code.
8. Developer Blind Spot: AI Over-Reliance and Insufficient Oversight
Issue:
- Developers increasingly accept AI output without scrutiny or validation.
- Time pressure or lack of domain expertise increases reliance on AI-generated code.
- Junior developers may lack the experience to question flawed logic or unsafe patterns.
- Teams may adopt AI suggestions wholesale without deeper contextual review.
Risk:
- Insecure, incorrect, or non-compliant code can silently enter production environments.
- Blind acceptance of AI output introduces logic bugs, missed validations, or broken flows.
- Lack of oversight may result in missed critical vulnerabilities or compliance failures.
- The erosion of manual code review culture weakens secure coding discipline and accountability.
The confidence in AI suggestions, especially from junior developers or under tight deadlines, creates automation bias. Developers may skip code review, fail to understand the logic, or even copy entire functions verbatim. This blind trust leads to code that works but is insecure or inappropriate for the application’s context.
9. Prompt Injection Threats: Tricking AI To Write Insecure Code
Issue:
- Attackers manipulate AI models through carefully crafted inputs or poisoned external content.
- Prompt injections may be hidden in user input, comments, documentation, or environment files.
- AI systems may lack validation mechanisms to differentiate between trusted and malicious inputs.
- Developers may unknowingly incorporate compromised instructions into their prompts or tools.
Risk:
- AI may output insecure code, leak credentials, or insert backdoors.
- Malicious logic can be introduced via indirect sources like README files or configuration metadata.
- Attackers can bypass intended constraints and force the AI to break guardrails.
- Prompt injections are difficult to detect, making exploitation stealthy and long-lasting.
Prompt injection attacks target the model’s instruction interface. This can be done through direct prompts (e.g., “ignore all security checks”) or indirectly through poisoned comments, README files, or config files. If the AI uses this poisoned context for generation, it can be tricked into inserting malicious logic.
10. Code Drift: Risks from AI Model Updates
Issue:
- AI model behaviour changes silently after backend updates by the provider.
- The same prompt may generate different results before and after a model upgrade.
- Developers may not be notified or may lack visibility into version-specific behavior.
- Codebases can unintentionally drift when teams unknowingly mix outputs from different model versions.
Risk:
- Stable code flows may break, causing runtime errors or business logic failures.
- Newly generated code may introduce regressions or security issues.
- Without model version tracking, teams cannot pinpoint the source of subtle bugs.
- Inconsistencies between environments or updates can reduce trust in AI tooling and affect team productivity.
As vendors retrain or update their LLMs, the same prompt may start producing different outputs. This “code drift” risks regressions, inconsistent styles, or reintroduction of old vulnerabilities. Teams that don’t track model versions or re-audit generated code risk silently accumulating flaws.
Mitigation Strategies: How to Build Secure AI-Assisted Software?
1. Robust Dependency Management
Use secure dependency management practices to reduce the risk of supply chain attacks:
- Utilize Dependency Management Tools like Github, pip etc.
- AI-suggested dependencies should be marked and verified against official repositories.
- Conduct regular audits and remove unused or outdated packages.
- Minimize third-party dependencies where ever feasible.
- Maintain SBOM and AI-BOM to track components and AI model versions. This can help during analysis and identification of issues related to dependencies.
2. Explicit Security Prompting
Train developers to guide AI tools with secure-by-default prompts:
- Include specifics like input validation, secure authentication, encryption standards.
- Use OWASP and SANS CWE aligned phrasing in prompts to generate secure codes.
- Avoid vague instructions like “build a login function.” Instead give detailed instructions like “Build a login function which complies with OWASP Authentication CheatSheet…”
- Leverage prompting to introduce obfuscation, validation, and injection resistance.
3. Mandatory and Context-Aware Human Code Review
Strengthen code reviews for AI-generated outputs:
- Mandate peer review for all AI-assisted contributions.
- Use tiered reviews for sensitive code (e.g., handling PII, cryptographic routines).
- Train reviewers to identify AI-specific anti-patterns and hidden vulnerabilities.
- Compliance and legal requirements should be identified during the design phase and should be part of the review process
4. Automated Security Scanning Tools in CI/CD
Integrate the following AI-aware security tooling:
- Static Application Security Testing (SAST) for pattern-based vulnerabilities.
- Secrets scanners for hardcoded credentials (e.g. GitGuardians etc.).
- Linters configured with security rules to identify and flag programming errors, bugs, stylistic inconsistencies, and suspicious constructs.
- Software Composition Analysis (SCA) tools to scan project dependencies
- Coding scanners to monitor for package level vulnerabilities (e.g. SonarCube, Veracode etc.)
- Dynamic Application Security Testing (DAST) for runtime issues.
- Data Loss Prevention (DLP) tools for sensitive prompt and data leakage monitoring.
5. Fine-Tuning AI Models with Enterprise Context
Improve contextual accuracy and reduce generic risks:
- Fine-tune LLMs / AI models on your organization’s secure private codebase, patterns, and standards.
- Include internal architectural guidelines, and naming conventions.
- Any standards or checklist related to compliance should be included fine tuning training data to reduce hallucinated suggestions and improves compliance alignment.
6. Developer Training and Awareness
Empower teams with secure AI coding skills:
- Educate developers on AI limitations and risks like prompt injection or over-reliance.
- Train them on secure prompt engineering techniques.
- Training materials should include relevant details about organization policies, risks associated with AI coding and associated anti-patterns, compliance requirements, mitigation strategies etc.
7. Strict Secrets Management Practices
Prevent accidental credential leaks:
- Ban use of hardcoded secrets in prompts or accepted output.
- Use secret managers, encrypted config files, and environment variables.
- Enforce scanning and removal of secrets pre-commit and pre-deployment.
- Code should be reviewed to ensure only the approved cryptographic standards are used
8. Secure-by-Design Integration
Embed security at every phase:
- Use threat modelling to identify AI generation threats and vulnerabilities related to data handling, access controls, or integration points
- Prompt AI to follow secure architecture constraints, such as enforcing authentication flows, role-based access, and secure data storage.
- Bake in least privilege, separation of duties principles, secure default, defence-in-depth and similar cybersecurity strategies. Strategies like Zero Trust Architecture can be helpful in reducing risks.
9. Clear Organizational Policies and Guardrails
Establish AI governance and guardrails:
- Define approved AI tools and their scope of usage.
- Require tagging of AI-generated code for traceability.
- Set policies for AI prompt content and data exposure.
- Limit AI context windows to trusted datasets where possible.
- Define which AI tools and Large Language Models (LLMs) are approved for use.
- Restrict AI use in sensitive systems unless explicitly reviewed.
- Require dependency vetting and model version tracking.
- Standard like ISO/IEC 42001 may help in setting up Effective AI management
The above organisational policies and guardrails can make AI code generation process more trustworthy.
10. Monitoring Model Updates and Re-Validation
Stay ahead of code drift:
- Track which AI model version generated which code.
- Re-test critical prompts after LLM upgrades.
- Monitor for subtle behaviour changes in AI-assisted code generation.
These strategies form a layered defence system that addresses both technical and human factors influencing AI Code Generation related software risks. Each tactic complements the others, ensuring security is built into every step of the AI code generation assisted development process.
Conclusion: AI Code Generation Tools Are Valuable, But With Caution
AI code generation assistants have proved their value and they bring real productivity benefits. But they have not been trained for security. Developers, tech leaders, product managers and organizations must remain vigilant, apply strong security processed and practices to create layered safeguards around AI-generated code. Identifying the risks of AI code generation and implementing mitigation strategies can help us in getting the productivity benefits of AI without sacrificing compromising the security posture of the software and the organization.

Good
Very good
Awesome
Very good
Awesome
Very good
Awesome
Very good
Awesome
Awesome
Very good