How Zero Trust Architecture moves security beyond the network walls of perimeter based security
Zero Trust Architecture (ZTA) is rapidly becoming one of the most prominent buzzwords in cybersecurity. As businesses accelerate cloud adoption, enable remote work, and face increasingly sophisticated cyberattacks, traditional perimeter-based defences are no longer enough. ZTA offers a fundamental shift—from assuming everything inside the network is trustworthy to verifying every user, device, and request, regardless of location. For cybersecurity leaders, this isn’t just a technology conversation—it’s a strategic pivot toward resilience, accountability, and proactive risk management.
While foundational guidance like NIST Special Publication 800-207 has brought structure to the Zero Trust conversation, the reality is that ZTA is still evolving. Vendor messaging is inconsistent, implementation patterns vary widely, and many business leaders are still unclear about what Zero Trust truly means beyond the buzz. In this blog, we cut through the noise to unpack ZTA from a strategic lens—explaining what it is, why it matters, the challenges it presents, and how leaders can adopt it effectively and sustainably.
Why Zero Trust?
Issues with Traditional Perimeter-Based Defences
For years, cybersecurity relied on the perimeter based defence approach: everything inside the enterprise network is trusted while those outside are blocked or scrutinized. That model was built for a time when users, devices, and data were all confined to a central, on-premises environment.
But that world no longer exists.
The perimeter is no longer clearly defined
- Users work remotely, often on personal or mobile devices.
- Applications and data are hosted in the cloud or across multiple vendors.
- Third parties regularly need access to internal systems.
One breach can expose everything
- Once attackers bypass the perimeter, they often have broad access to internal systems.
- Traditional security models don’t verify each access request within the network.
- Insider threats and stolen credentials can be exploited with minimal resistance.
Visibility and control are limited
- Legacy tools offer weak monitoring of remote users, cloud apps, or BYOD environments.
- It’s difficult to enforce consistent security policies across hybrid infrastructure.
- Logs and audit trails often lack the depth needed for real-time response.
Traditional models aren’t built for modern threats
- Sophisticated attacks like ransomware, phishing, and advanced persistent threats can bypass outdated defences.
- Static, location-based trust decisions don’t adapt to real-time risk signals.
- Security becomes reactive rather than proactive.
Zero Trust Architecture eliminates these weaknesses by removing implicit trust. Every access request is verified in real time—based on identity, device health, and context—before access is granted. It’s a security model designed for how modern businesses actually work.
But modern problems need modern defences.
Enter Zero Trust!!! A new way of thinking. A bold shift in strategy. And exactly what today’s security challenges demand.
What is Zero Trust and How It Helps?
Zero Trust Architecture (ZTA) is not a single technology or product—it’s a security philosophy built on the understanding that trust should never be assumed, and that threats can originate from anywhere, at any time.
At its core, Zero Trust helps organizations reduce risk, limit exposure, and maintain control—by enforcing strict access decisions, continuous validation, and minimizing the impact of potential breaches.
Following are the key foundational principles of Zero Trust and how they help:
1. Never trust, always verify
Every access request is treated as potentially hostile. No user or device is trusted by default, even if they’re inside the network.
2. Use micro-segmentation
The network is broken into smaller, isolated zones to prevent lateral movement. Even if one part is compromised, the threat doesn’t spread easily.
3. Leverage least privilege access
Users, applications, and devices get only the minimum access they need—nothing more. This limits what an attacker can do if they gain access.
4. Assume breach by default
Security posture is built on the expectation that breaches can and will happen. This mindset drives proactive defence and faster containment.
5. Continuously monitor and analyse behaviour
Ongoing analysis of user and device activity helps detect anomalies early—before they become full-scale incidents. Monitoring network traffic and efficient loggings are key to successful ZTA deployment.
6. Verify identity continuously
Authentication isn’t a one-time event. Identity is validated at every step, using contextual factors like role, location, and risk level. Identify and access decisions may change dynamically based context.
Key Components of Zero Trust Architecture (ZTA)
Implementing Zero Trust isn’t just about adopting new tools—it requires a well-defined architecture with clearly structured components that work together to enforce continuous verification and context-aware access control.
NIST Special Publication 800-27 defines the following components of a Zero Trust Architecture:
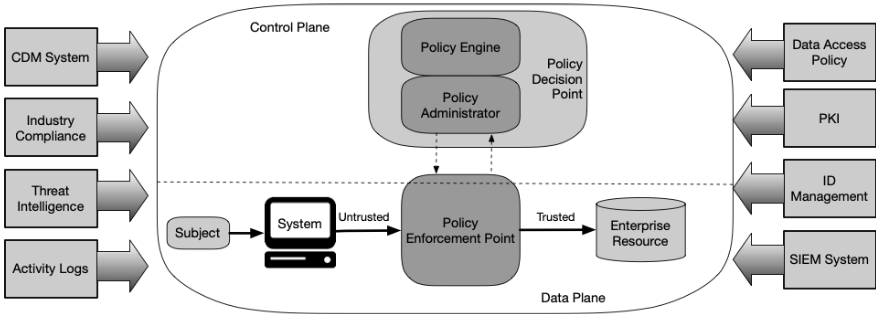
Source: Key Components of Zero Trust Architecture (ZTA) [Source: NIST SP 800-27]
1. Policy Engine (PE)
The Policy Engine makes the ultimate decision on whether access should be granted or denied. It evaluates real-time inputs such as identity, device posture, location, behaviour patterns, and threat intelligence.
2. Policy Administrator (PA)
The Policy Administrator acts on the decisions from the Policy Engine. It establishes or terminates communication paths between users and resources, typically by configuring network or application-level access policies.
3. Policy Enforcement Point (PEP)
This is where access decisions are enforced. The PEP intercepts requests from users or devices and ensures only authorized connections are allowed—based on policies set by the PE and PA. PEPs can exist on endpoints, applications, or network gateways.
4. Identity Management System
This system verifies who the user is, often using multi-factor authentication (MFA), single sign-on (SSO), and contextual factors such as user role, behaviour, or risk signals.
5. Device Security and Posture Management
ZTA continuously validates whether a device is compliant, secure, and up to date before allowing access. This includes checking for malware, software versions, encryption status, and more.
6. Continuous Monitoring and Analytics
Behavioural analytics, SIEMs (Security Information and Event Management), and user activity logs feed into the architecture to support anomaly detection and policy refinement.
7. Data Access Policies
Data classification and sensitivity inform how access is granted. These policies ensure that the principle of least privilege is applied—not just to systems, but to the specific data being accessed.
8. Trust Algorithm
The decision logic used by the Policy Engine to weigh factors such as identity confidence, device posture, threat level, location, and user behaviour. It dynamically determines access outcomes based on risk. Inputs come from sources like identity systems, EDR tools, SIEMs, threat intelligence feeds, and continuous monitoring platforms.
However just having the components together are not sufficient. Cybersecurity leaders must be aware of the key success factors for the implementation of ZTA!
Success Factors for ZTA Implementation.
Successfully implementing Zero Trust is not just about technology—it requires alignment across people, processes, and platforms. Organizations that achieve meaningful results with ZTA typically have several foundational elements in place.
Here are the key factors critical to ZTA success:
1. Strong Identity and Access Management (IAM)
Robust IAM ensures that users are who they claim to be, with access tailored to their roles. Multi-factor authentication (MFA) and identity federation are essential.
2. Visibility Across Users, Devices, and Workloads
Continuous monitoring and integrated telemetry help detect abnormal activity and drive real-time access decisions.
3. Secure and Compliant Device Posture
Only trusted, up-to-date, and policy-compliant devices should be allowed to connect. Device posture must be continuously evaluated.
4. Business Process and Workflow Mapping
Understanding how people work, which systems they access, and what data they handle is foundational. Mapping these workflows helps define least-privilege access policies, identify high-risk interactions, and avoid breaking productivity with overly rigid controls.
5. Well-Defined Data and Resource Classification
Clear classification of data and digital assets ensures that policies are applied based on sensitivity and business impact.
6. Scalable and Resilient Policy Infrastructure
Policy Engines, Administrators, and Enforcement Points must operate at scale without creating bottlenecks or single points of failure.
7. Cultural Buy-In Across Business and IT
ZTA needs executive backing and active collaboration across security, IT, and business units. Without shared ownership, implementation often stalls.
8. Continuous Policy Optimization
Access rules must evolve with user behaviour, threats, and organizational change. Data from monitoring systems should feed back into policy updates.
However, like any change even ZTA adoption does not comes without it’s risks. Cybersecurity leaders should be aware of these risks and address them since the beginning.
Key Risks and Downside of ZTA Adoption
While Zero Trust offers a modern and resilient security model, its implementation is not without challenges. Organizations must be aware of the potential risks and downsides to ensure a smooth and sustainable adoption.
Here are some of the key risks to consider:
1. Complex Integration Across Micro-segments
Integrating Zero Trust principles into environments containing multiple micro-segments that mix legacy systems, on-prem applications, and cloud services can be technically complex. Many older systems may not support modern identity protocols or API-based access controls, requiring costly workarounds or upgrades.
2. Lack of Unified Vendor Ecosystem
There is no single vendor that delivers a complete ZTA out of the box. Enterprises often need to stitch together solutions from multiple providers—each with its own architecture, standards, and interoperability constraints. This fragmentation can delay implementation and increase operational overhead.
3. Potential User Friction
Without careful design, Zero Trust controls—like frequent reauthentication or strict access limits—can frustrate end users and hinder productivity. Poor user experience can lead to shadow IT workarounds or disengagement from secure processes.
4. New Attack Surfaces on Core ZTA Components
ZTA introduces new attack surfaces and single point of failures like the Policy Engine, Policy Administrator, and Enforcement Points become high-value targets. A denial-of-service (DoS) attack on these elements could disrupt access across the enterprise. Resilience and redundancy planning is critical.
5. Risk of Misconfiguration
Trying to apply Zero Trust principles everywhere at once can lead to overly complex policies, increased false positives, or system disruptions. Misconfigurations may accidentally block critical access, impacting operations or availability.
6. High Initial Resource Investment
ZTA requires significant upfront effort in identity mapping, device posture enforcement, workflow analysis, and tool integration. Smaller organizations may struggle with the skills, time, or budget needed for implementation.
7. Skill Gaps and Change Resistance
Zero Trust adoption requires a shift in mindset and skills. Security teams must understand identity-centric security models, dynamic policies, and telemetry-driven decisions. Business units may resist perceived complexity or changes to how work gets done.
ZTA is a powerful model—but not a plug-and-play solution. Understanding these risks upfront allows organizations to plan realistically, build resilience, and avoid the common pitfalls of over-promising and under-delivering.
How to Mitigate the Risks of Zero Trust Adoption
While Zero Trust Architecture (ZTA) introduces a new level of security maturity, its implementation demands thoughtful planning and coordination. The good news? Most risks can be mitigated with the right mix of strategy, design, and stakeholder alignment.
Here’s how to address the most common pitfalls:
1. Start with a Pilot, Not a Big Bang
Begin Zero Trust implementation by applying policies to a small, well-defined group of enterprise resources, users (subjects), and workflows. This controlled scope allows for validating the behavior of the Policy Engine, Policy Administrator, and Enforcement Points without disrupting broader operations.
This phased approach supports:
- Clear definition of trust boundaries (protect surface)
- Iterative refinement of access policies
- Gradual integration of identity, telemetry, and policy systems
2. Prioritize Interoperability and Vendor Fit
Select tools that support open standards and integrate smoothly into your existing identity, endpoint, and cloud ecosystems. Favor modular platforms over tightly coupled stacks.
3. Map Workflows and Access Patterns Early
Understand who accesses what, from where, and under which circumstances. Map data flows and business processes to avoid blind spots and policy friction.
4. Design for User Experience
Leverage password less authentication, SSO, and adaptive policies to ensure strong security without frustrating end users.
5. Build Resilience into Core ZTA Components
Ensure redundancy and high availability for critical components like Policy Engines, Policy Administrators, and Enforcement Points. Incorporate DDoS protection and failover mechanisms.
6. Make Integrations Easy and Future-Proof
ZTA success depends on seamless integration across identity, network, endpoint, and analytics systems. Ensure your selected tools offer robust APIs, SDKs, or integration wrappers to connect with existing infrastructure. During vendor selection, negotiate for interoperability and avoid hard dependencies that create long-term lock-in risks. Favor platforms that support plug-and-play architecture, modular upgrades, and third-party extensibility.
7. Invest in Education and Change Management
Equip both technical and non-technical teams with the knowledge to support Zero Trust initiatives. Help users understand the “why,” not just the “how.”
8. Maintain Continuous Governance and Optimization
Continuously monitor, refine, and adapt policies using threat intelligence, behavior analytics, and real-time insights from your ZTA stack.
9. Choose the Right ZTA Deployment Model
NIST SP 800-207 outlines several deployment patterns—Device Agent/Gateway, Enclave-Based, Resource Portal, and Application Sandboxing. Selecting the right model for your environment (e.g., legacy systems, remote workforces, or cloud-native workloads) ensures faster implementation and better risk alignment.
With the right approach, Zero Trust becomes less of a risk—and more of a long-term strategic advantage.
BONUS: Questions Cybersecurity Leaders Should Ask for ZTA!!
Adopting Zero Trust Architecture (ZTA) requires more than a technical deployment—it demands a fundamental rethinking of how trust, access, and security are managed across the enterprise. Cybersecurity leaders must ask the right questions early to drive clarity, avoid pitfalls, and align the initiative with business value.
Here are the key questions to consider:
1. What are our most critical business processes and assets, and who needs access to them?
Understanding workflows and access dependencies is essential to apply least privilege and avoid disrupting operations.
2. Which ZTA deployment model fits best with our current infrastructure and maturity level?
Choosing between device agent, enclave-based, portal-based, or hybrid models can significantly impact implementation speed and effectiveness.
3. Do we have the right identity, device, and telemetry systems in place to support dynamic access decisions?
ZTA depends on continuous data from multiple sources. Gaps here will limit effectiveness.
4. How will we define and enforce trust criteria in real time?
This includes policies for user behaviour, device posture, risk scoring, and environmental factors.
5. Are our core ZTA components—Policy Engine, Policy Administrator, and Enforcement Points—resilient and scalable?
Downtime or failure in these systems could cause widespread access issues.
6. How do we ensure business continuity and user experience while implementing Zero Trust controls?
Security should not come at the cost of productivity. Balance is key.
7. How will we measure success?
Define metrics for reduction in attack surface, policy enforcement accuracy, incident response time, and user adoption.
8. Are our vendors interoperable and aligned with open standards?
A fragmented tech stack can create complexity. Prioritise interoperability and long-term flexibility.
9. Do we have the internal expertise, or will we need external support to design and implement ZTA?
Skill gaps can delay or derail progress. Planning for enablement or partnerships is essential.
10. Are we treating Zero Trust as a long-term strategic shift, not a short-term project?
Sustainable success depends on cultural change, ongoing governance, and iterative improvement.
11. Are we negotiating the right vendor terms to support flexibility and reduce lock-in risk?
Zero Trust implementations often require a mix of tools from different vendors. Leaders must ensure contracts allow for integration via APIs, modular deployment, and data portability. Ask vendors about support for open standards, exit strategies, and future-proofing. Negotiate terms that allow your organization to adapt, scale, or switch providers without excessive cost or technical rework.
These questions are not just the starting point but they set strategic compass for cybersecurity leaders to implement Zero Trust to achieve enhanced control together with reduced risk, optimized convenience and increased business productivity.
Conclusion
Zero Trust Architecture is more than a cybersecurity trend—it represents a necessary shift in how organizations approach trust, identity, and access in a borderless digital world. As devices and attack surfaced start moving out of traditional perimeter defences, ZTA offers a forward-looking model built on continuous verification, least privilege, and contextual awareness.
However, implementing Zero Trust is not a one-size-fits-all solution. It requires thoughtful planning, stakeholder alignment, flexible integration, and a clear understanding of your organization’s workflows, risks, and priorities.
When Done right, Zero Trust doesn’t just reduce risk – it’s the difference between chaos and control.